Witcher: Managing GitHub Advanced Security (GHAS) Controls at Scale
Note: This article was authored by me and originally published on Moonfare’s Official Blog as part of my work at Moonfare. It is republished here on my personal blog with permission.
This post explores the limitations of GitHub Advanced Security (GHAS) and how Witcher enhances security management by providing greater scalability, control, and efficiency across repositories.
An Introduction to GitHub Advanced Security (GHAS)
GitHub Advanced Security (GHAS) is a comprehensive security suite that enhances code security. It offers a range of features that integrate directly into the development workflow, protecting at the pull request (PR) level to identify and mitigate vulnerabilities early.
GitHub Advance Security comes with the following features
- Code scanning
- CodeQL CLI
- Secret scanning
- Custom auto-triage rules
- Dependency review
You can read more about each feature here.
GitHub Advanced Security is available at no cost for public repositories, while a license is required to enable its features for private repositories.
The Challenges of Managing Security Controls at Scale
When working in an organization with several hundred repositories, deploying and implementing security controls across all of them can become a significant challenge. The GitHub Advanced Security dashboard and Code security configurations are not sufficient when security controls need to be applied to a specific subset of repositories such as 200 from 500 repositories.
Also, Not all repositories are directly related to production or the core application code, and GitHub primarily offers the ability to apply security controls either across all repositories or with limited configuration options. This lack of granular control makes it difficult to tailor security controls to different types of repositories within an organization.
Manually setting up security controls like CodeQL, image scanning, or Infrastructure as Code (IaC) scanning across a subset of repositories in a large organization isn’t just time-consuming but also it’s hard to manage at scale. The real challenge goes beyond deployment; keeping track of what’s enabled, ensuring consistency, and continuously monitoring security findings becomes increasingly difficult as the number of repositories grows.
This is where the GitHub Advanced Security dashboard has limitations. While it provides organization-wide visibility, it lacks the flexibility to track security controls for a specific subset of repositories, making it challenging to monitor adoption, findings, and enforcement effectively.
The lack of granular control and visibility makes it challenging for security teams to enforce policies across critical repositories. Without a targeted approach, organizations struggle to prioritize high-risk repositories, track security adoption, and ensure compliance. In such cases, additional tools or automation are crucial for effective security management at scale.

Witcher - your new best friend
Witcher is a tool designed to streamline and automate security control management for GitHub repositories. Whether you’re enabling CodeQL, Dependabot, Secret Scanning, or managing Infrastructure as Code (IaC) scanning, Witcher empowers you to easily implement and monitor security features across multiple repositories.
With Witcher, you can:
- Perform mass actions across repositories, such as enabling, deploying, or deleting security controls.
- Get daily security summaries to stay up to date.
- Integrate with Slack for real-time alerts and Jira to create tickets for vulnerabilities.
- Log all changes and activities on SIEM for tracking and custom dashboards
- Manage workflows and repository configurations at scale, ensuring your security posture remains strong across all your GitHub repositories.
Witcher is designed to help security teams tackle the challenges of managing large numbers of repositories, ensuring consistency, efficiency, and visibility across your entire GitHub environment.
Setup witcher
$ git clone git@github.com:mf-labs/witcher.git
$ cd witcher
$ npm i
Here’s a quick look at the available options:
➜ witcher git:(master) node witcher.js -h
usage: witcher.js [-h] -m MODULE -a ACTION [--daily-summary] [--mass-action] [--slack] [--siem] [--jira]
[--jira-ticket JIRATICKET] [--org ORG] [-r REPO] [-b BRANCH]
[--workflow-file WORKFLOW] [--repo-file REPOFILE]
witcher ....... you can't escape
optional arguments:
-h, --help show this help message and exit
-m MODULE, --module MODULE
ghas, dependabot, secret-scanning, codeql, iac, workflows, ALL
-a ACTION, --action ACTION
enable, disbale, status, alert, deploy, delete
--daily-summary Get the Daily Summary
--mass-action Perform action (enable, deploy, delete) at scale
--slack Post new alert(s) on Slack
--siem Log activities on SIEM
--jira Post new vulnerability ticket on Jira
--jira-ticket JIRATICKET
Jira ticket ID (e.g. PROJECT-123)
Input:
--org ORG Organization Name
-r REPO, --repo REPO Repository Name, ALL
-b BRANCH, --branch BRANCH
Branch Name
--workflow-file WORKFLOW
Workflow File Name
--repo-file REPOFILE Repo File Name
Witcher is your go-to tool to bring granular control and automation to your GitHub Advanced Security workflow, saving you time and ensuring a robust security posture at scale.
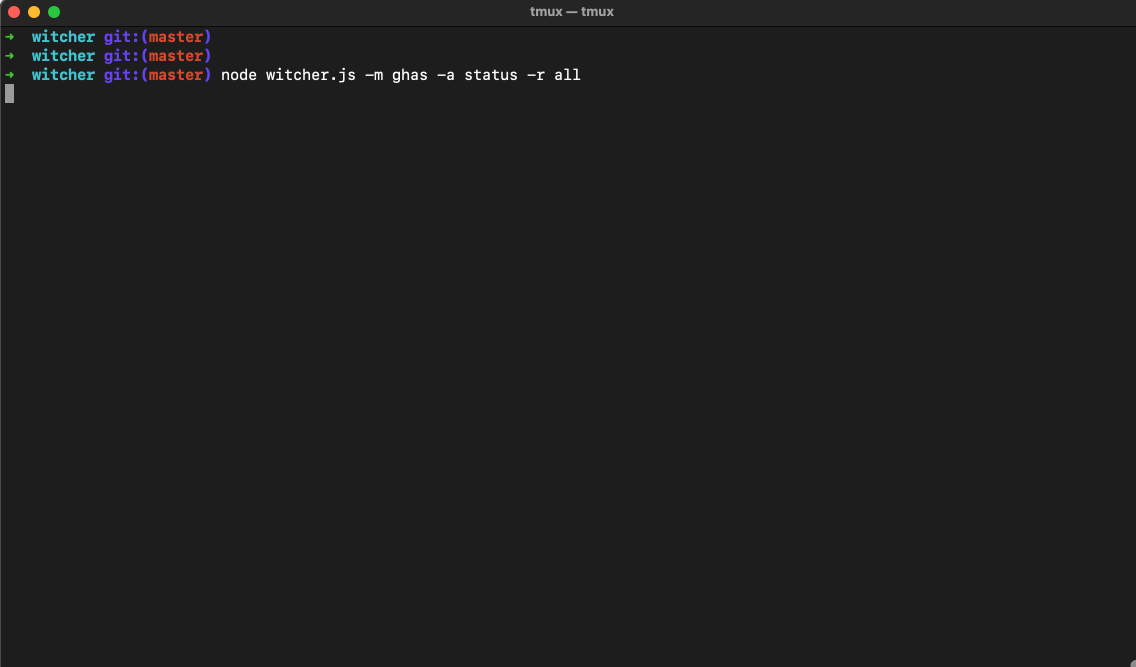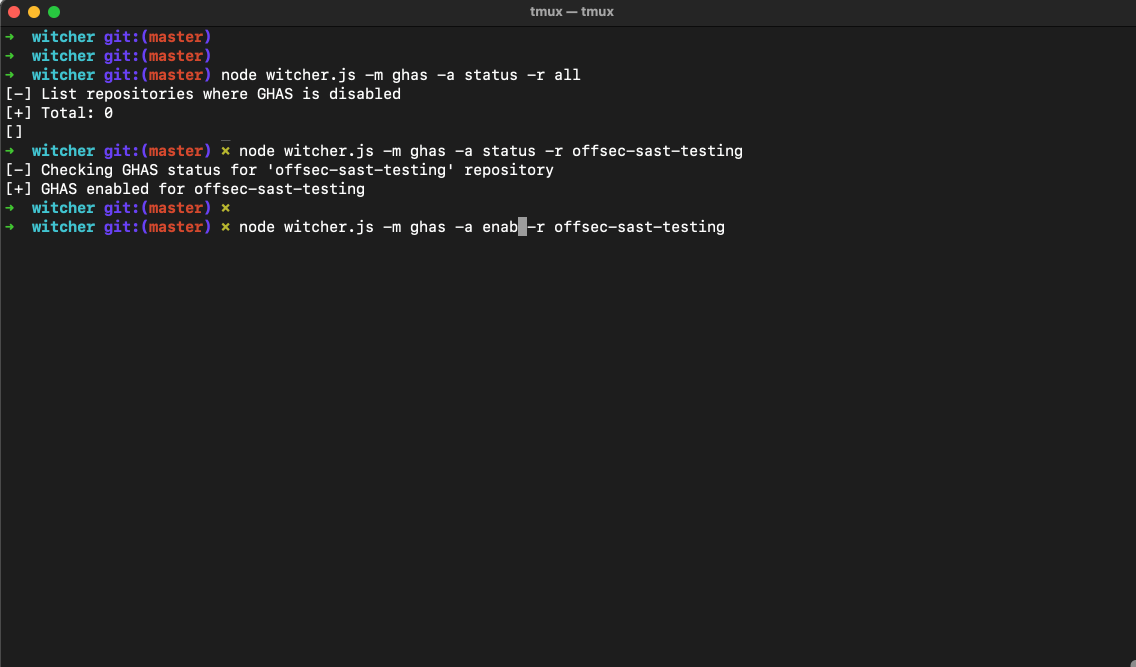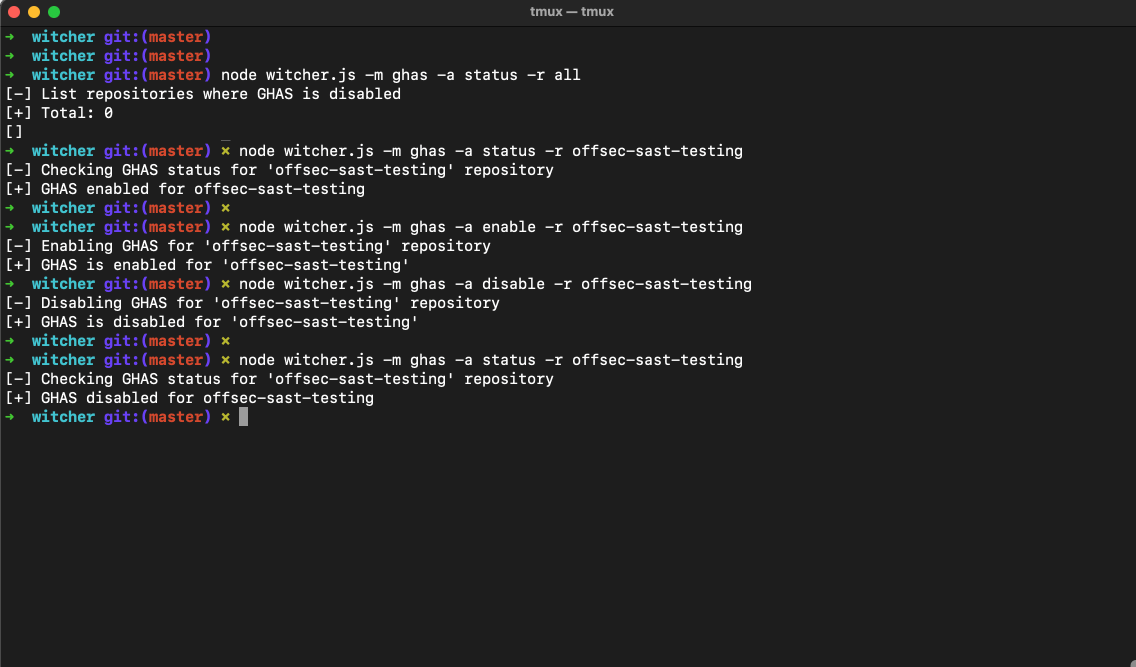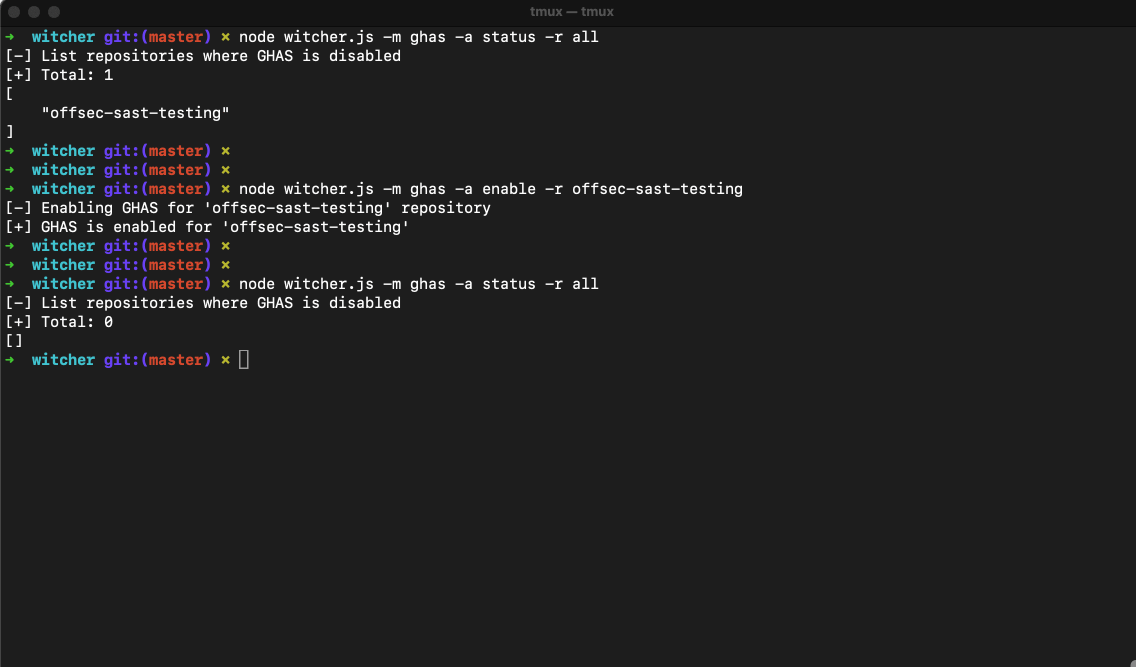
Witcher Daily Summary
The daily summary includes crucial information such as the status of GHAS, Secret Scanning, Dependabot, Code Scanning (CodeQL), and IaC Scanning. It even highlights specific issues, like repositories where Dependabot is paused, giving security teams a quick snapshot of the security health of their codebase. With Witcher, teams can easily monitor their security posture, track adoption, and ensure that everything is running smoothly.
# Run Daily Summary
$ node witcher.js --daily-summary -m ALL -a status --slack --jira
Here’s an example of what your daily summary could look like:
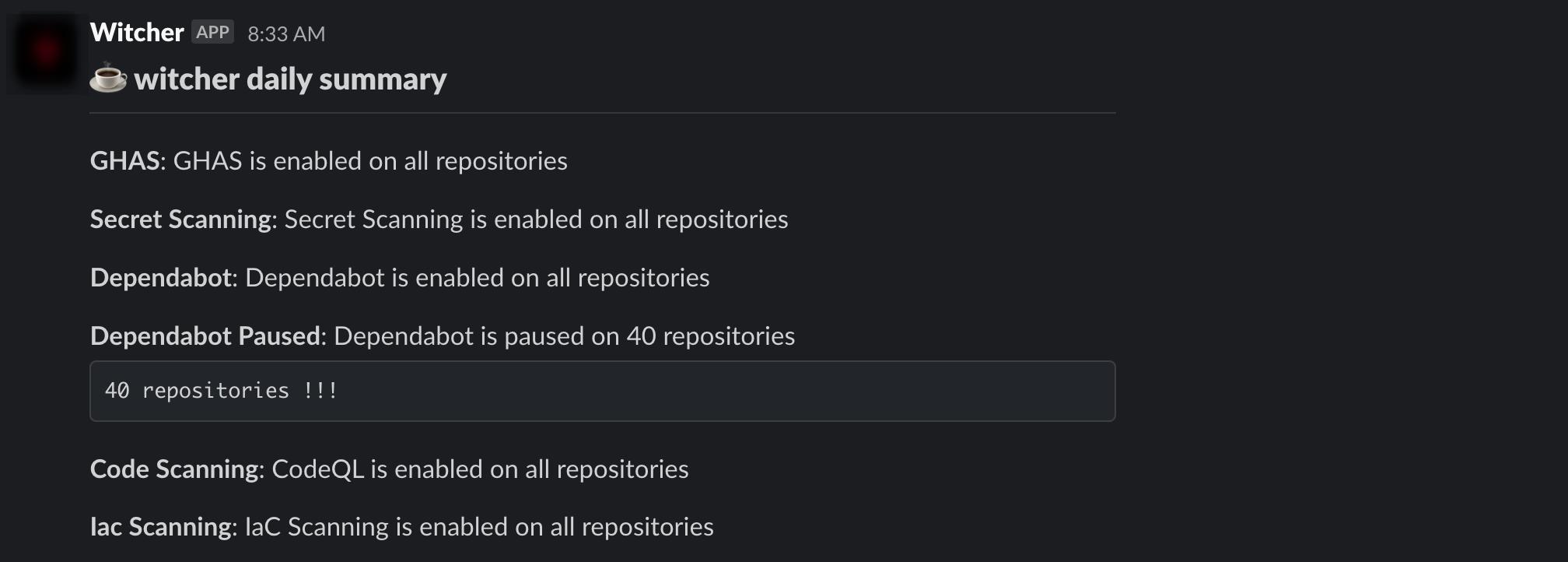
With Witcher’s daily updates, your security team gets the insights they need to stay on top of security controls across all repositories without any extra manual work.
Witcher also actively monitors for new vulnerability findings across your repositories on a daily basis. Whenever a new issue is detected, Witcher generates a detailed vulnerability alert and creates a corresponding Jira ticket, so your team can quickly take action.
Configure a daily routine by using this GitHub Action.
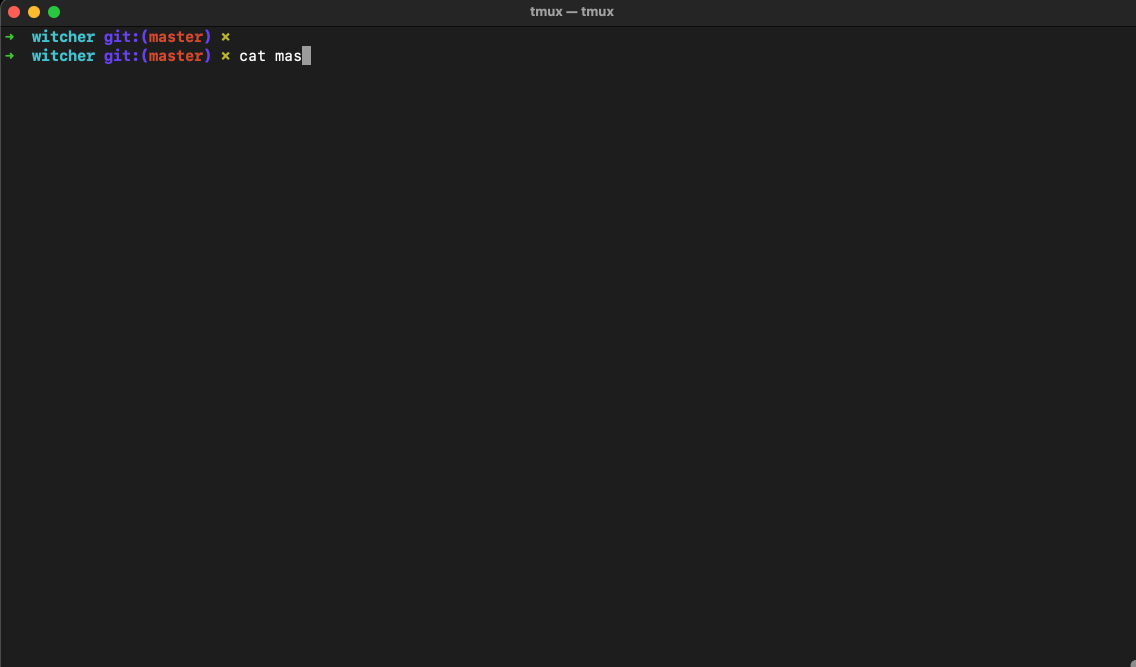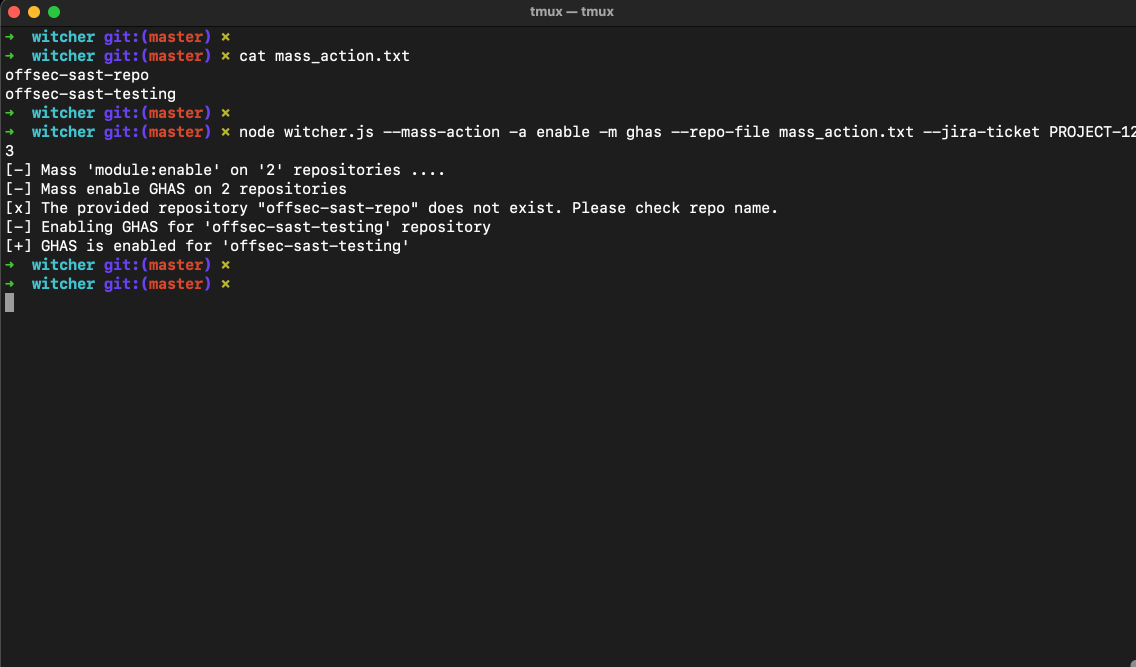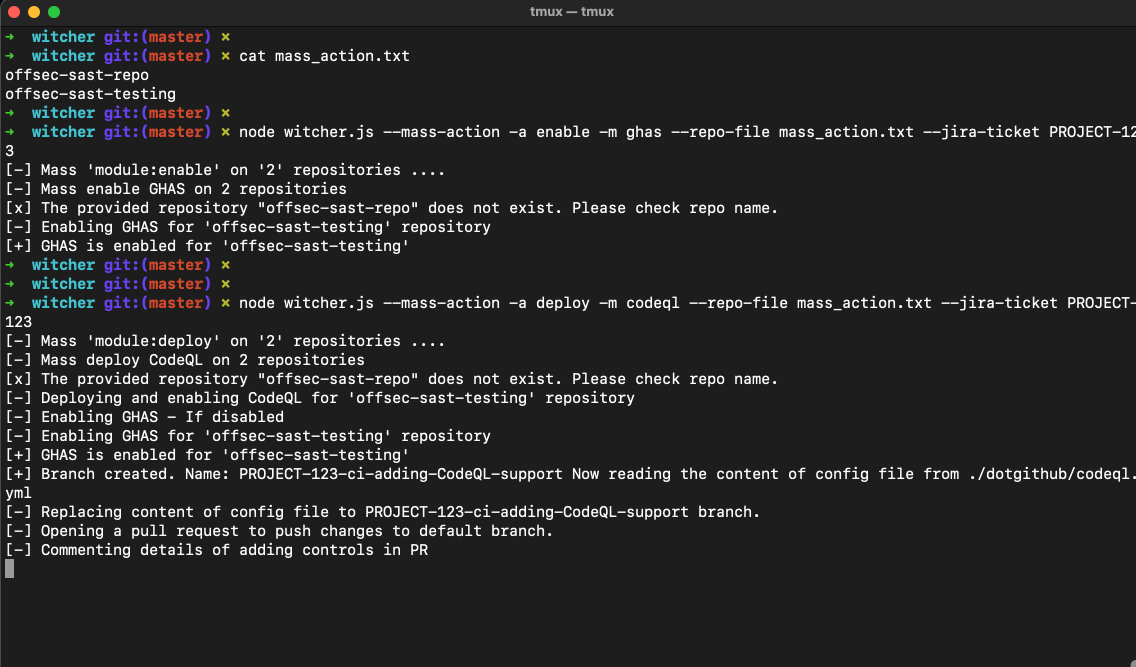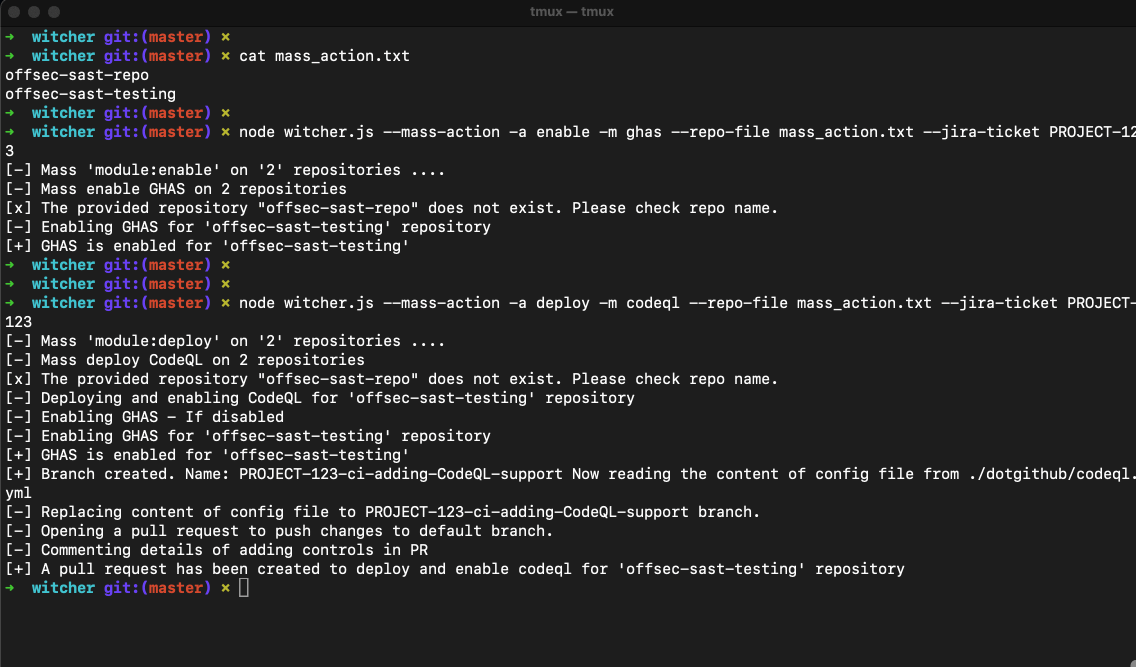
Witcher Mass Action
When dealing with hundreds of repositories, performing security changes one at a time is impractical. Mass Action allows you to:
- Enable or disable GHAS, Secret Scanning, Dependabot and CodeQL across multiple repositories instantly.
- Deploy or Delete CodeQL and Dependant .yml file at scale.
- Ensure all changes and PRs are tracked in SIEM for visibility and auditing.
# Disable GHAS on multiple repositories
$ node witcher.js --mass-action -a disable -m ghas --repo-file mass_action.txt --jira-ticket PROJECT-123
# Enable GHAS on multiple repositories
$ node witcher.js --mass-action -a enable -m ghas --repo-file mass_action.txt --jira-ticket PROJECT-123
# Deploy CodeQL (custom yml) file on multiple repositories
$ node witcher.js --mass-action -a deploy -m codeql --repo-file mass_action.txt --jira-ticket PROJECT-123
# Delete dependabot (custom yml) file from multiple repositories
$ node witcher.js --mass-action -a delete -m dependabot --repo-file mass_action.txt --jira-ticket PROJECT-123
Apart from mass action, witcher also works on a single repository.
# Disable GHAS on <repo-name>
$ node witcher.js -m ghas -a disable -r <repo-name>
# Checking Secret Scanning status for '<repo-name>' repository
$ node witcher.js -m secret-scanning -a status -r <repo-name>
# Get latest code scanning vulnerability (with 1 day difference)
$ node witcher.js -m codeql -a alert --slack // --slack to post on slack
# Implement CodeQL on <repo-name>
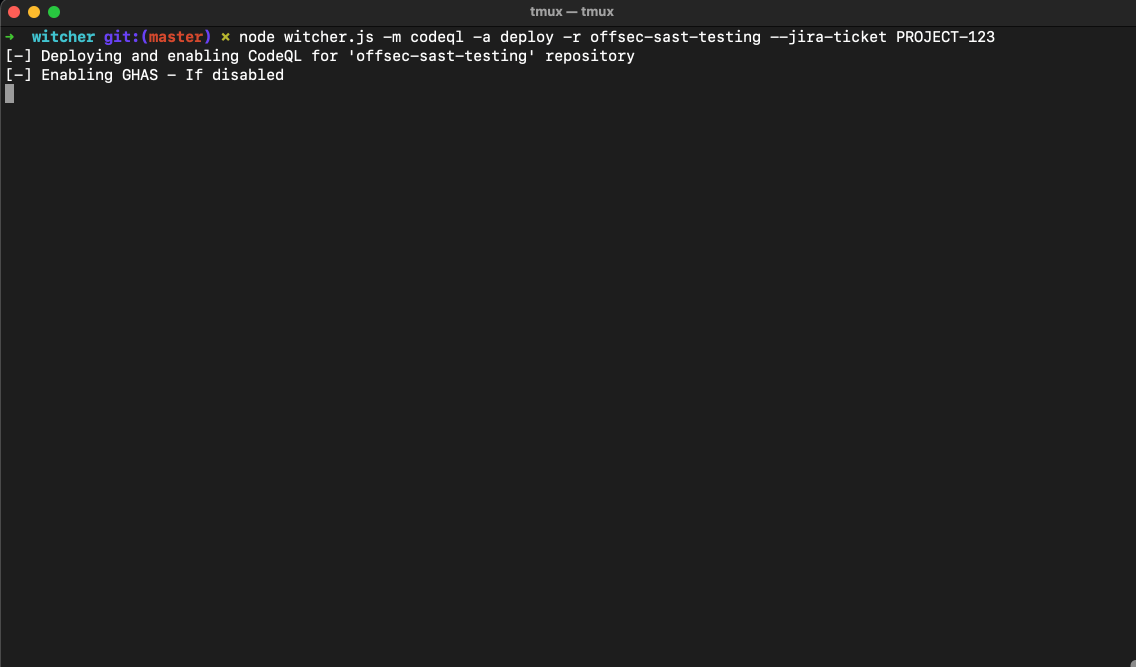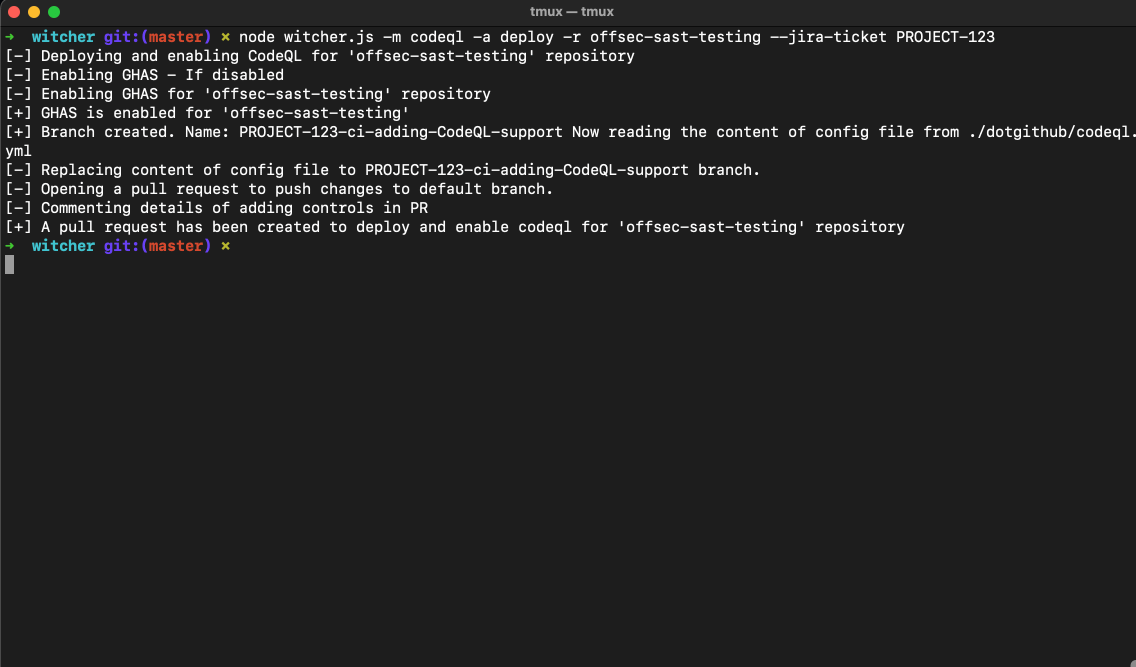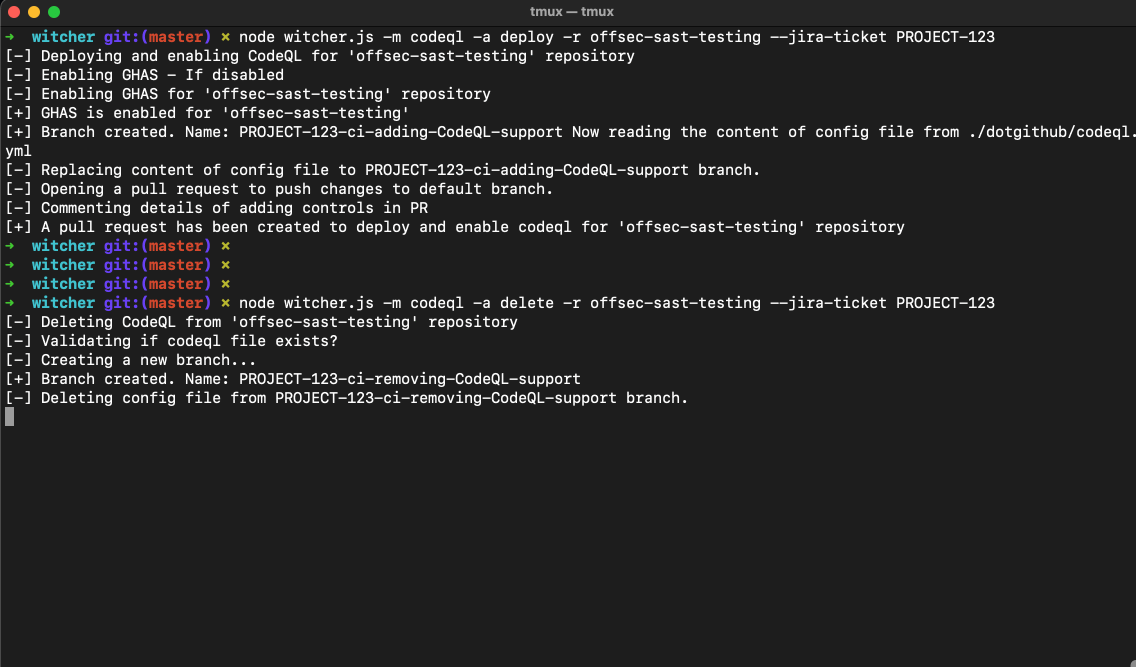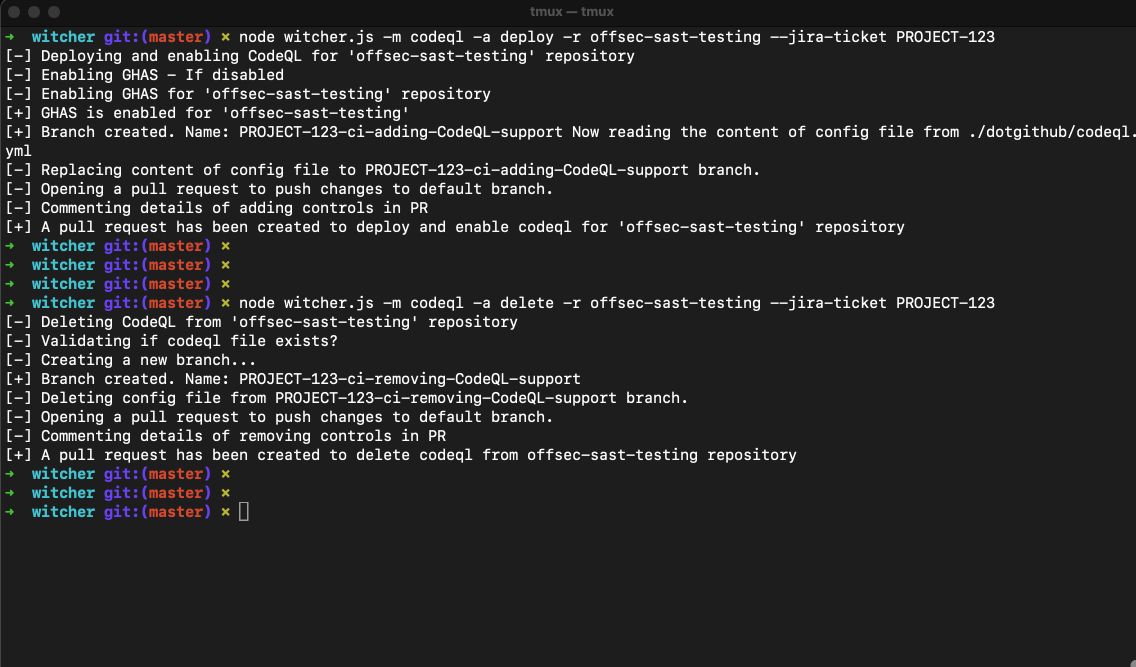
$ node witcher.js -m codeql -a deploy -r <repo-name> --jira-ticket PROJECT-123
# Remove CodeQL from <repo-name>
$ node witcher.js -m codeql -a delete -r <repo-name> --jira-ticket PROJECT-123
The deploy / delete actions create a PR to corresponding repositories for implementing / removing targetted yml file.
Logging Witcher activities on SIEM for Custom Dashboards
For complete visibility into the security automation efforts to track, analyze, and optimize the workflows. Witcher, log all key activities, including daily summaries, pull requests (PRs), and security actions, directly into SIEM using Serverless Application / Webhooks. This integration allows teams to build custom dashboards, providing real-time insights into security posture and all other activities.
Witcher can record the following logs
-
Daily Summary
-
Logging of actions performed by witcher
-
Logging of PRs created by witcher
SIEM integration is disabled by deafult on this release, you can enable it by changing
logOnSIEM = truein./utils/siem.jsor by providing--siemflag via CLI.
References
- https://github.com/mf-labs/witcher
- https://docs.github.com/en/get-started/learning-about-github/about-github-advanced-security